Global Models address targets of opportunity
BENEFITS
Deploy model in minutes
Near real-time risk scores
Unmatched efficiency gains over scanners
Identify real-time risks
Decrease false negatives
Local Models address targeted attacks
BENEFITS
Model adapts to telemetry & intel controls
Only accessible by your organization
Achieve data completeness
Make real-world contextual decisions
Provide defensible evidence for regulators
Our Dataset
Empirical monitors activity on over 17,000 exploited CVEs—10 times more than the next best model—and offers hourly exploitation evidence and volume, an industry first.
17,000+ Known Exploit Vulnerabilities
Near Real-Time Exploitation Activity
Hourly Telemetry per CVE (going back years)
Millions of Malware Hashes related to CVEs
Over 1,400 OSINT Sources (Open-Source Intelligence)
How We Help
Organizations use our data and models to make smarter decisions.
Modular Solutions
Flexible by Design
Augment your in-house vuln scoring system with our global models.
Team Alignment
Shared Understanding
Compare risk thresholds before making decisions that impact your team.
Validate Findings
True Local Context
Our local models validate findings with evidence backed by your telemetry.
Elevate Conversations
Mature your Organization
Reduce and justify workload (capacity) with our local models.
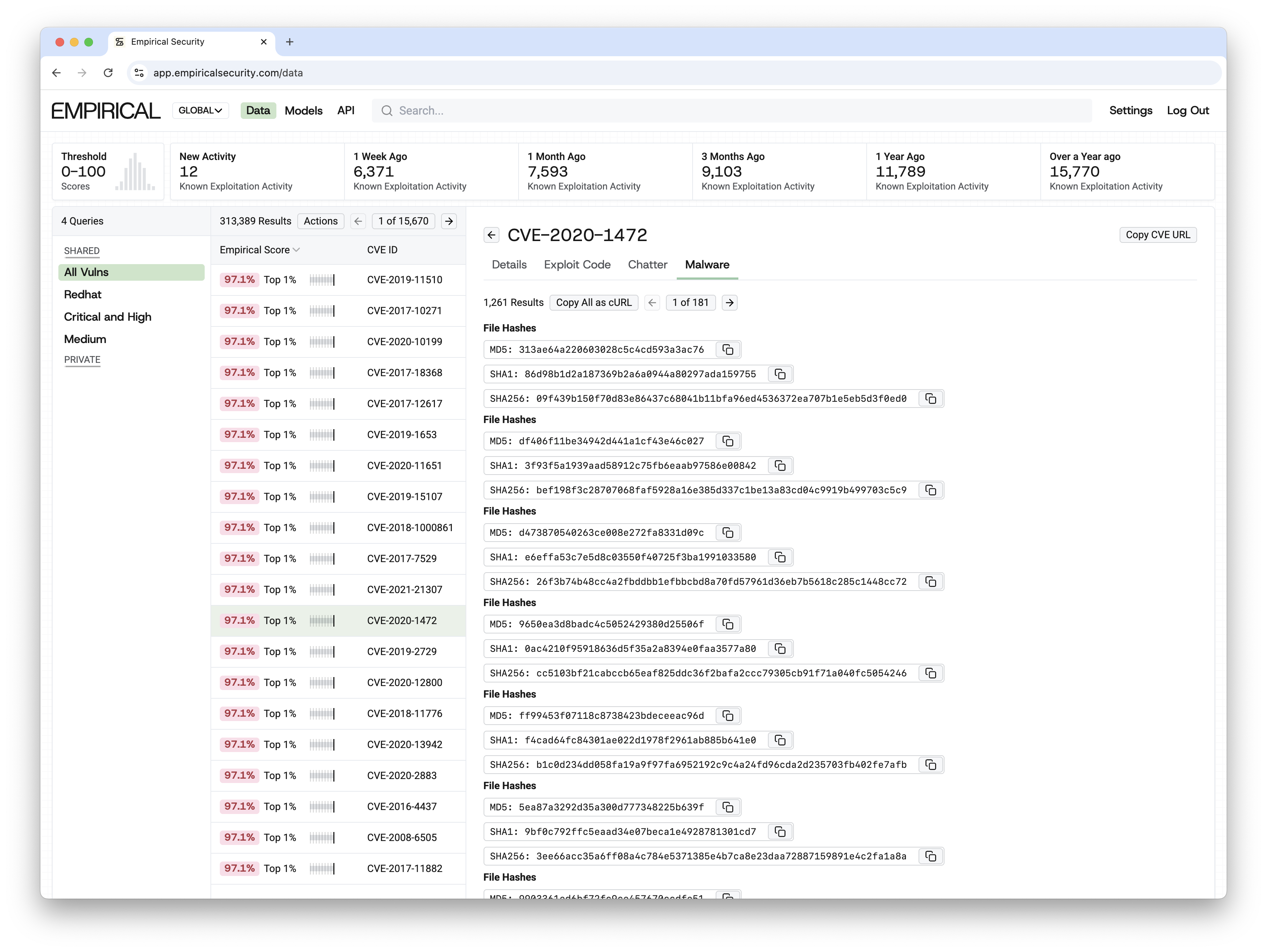
Real-Time Known Exploitation Activity
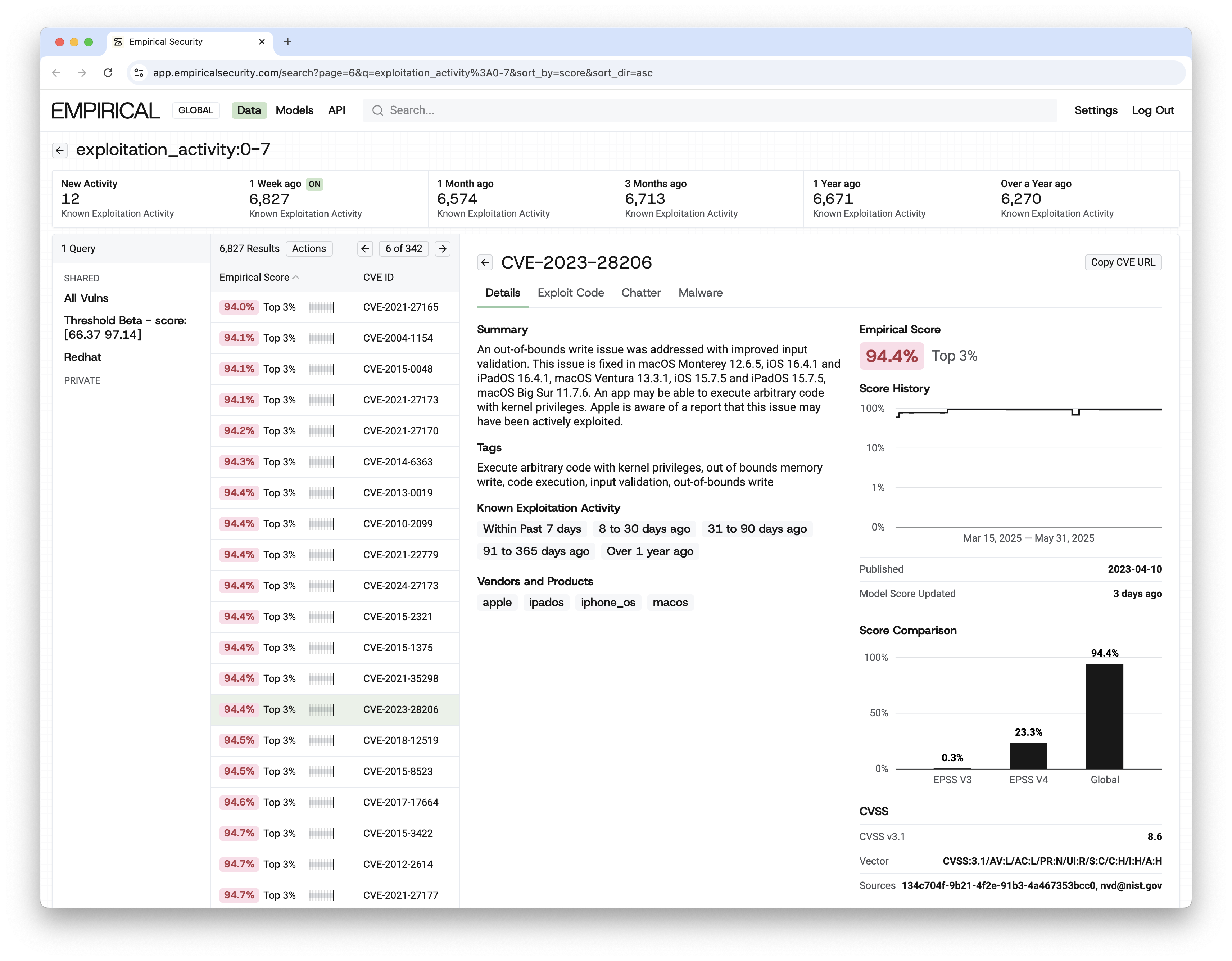
Exploit Code Discovery Model
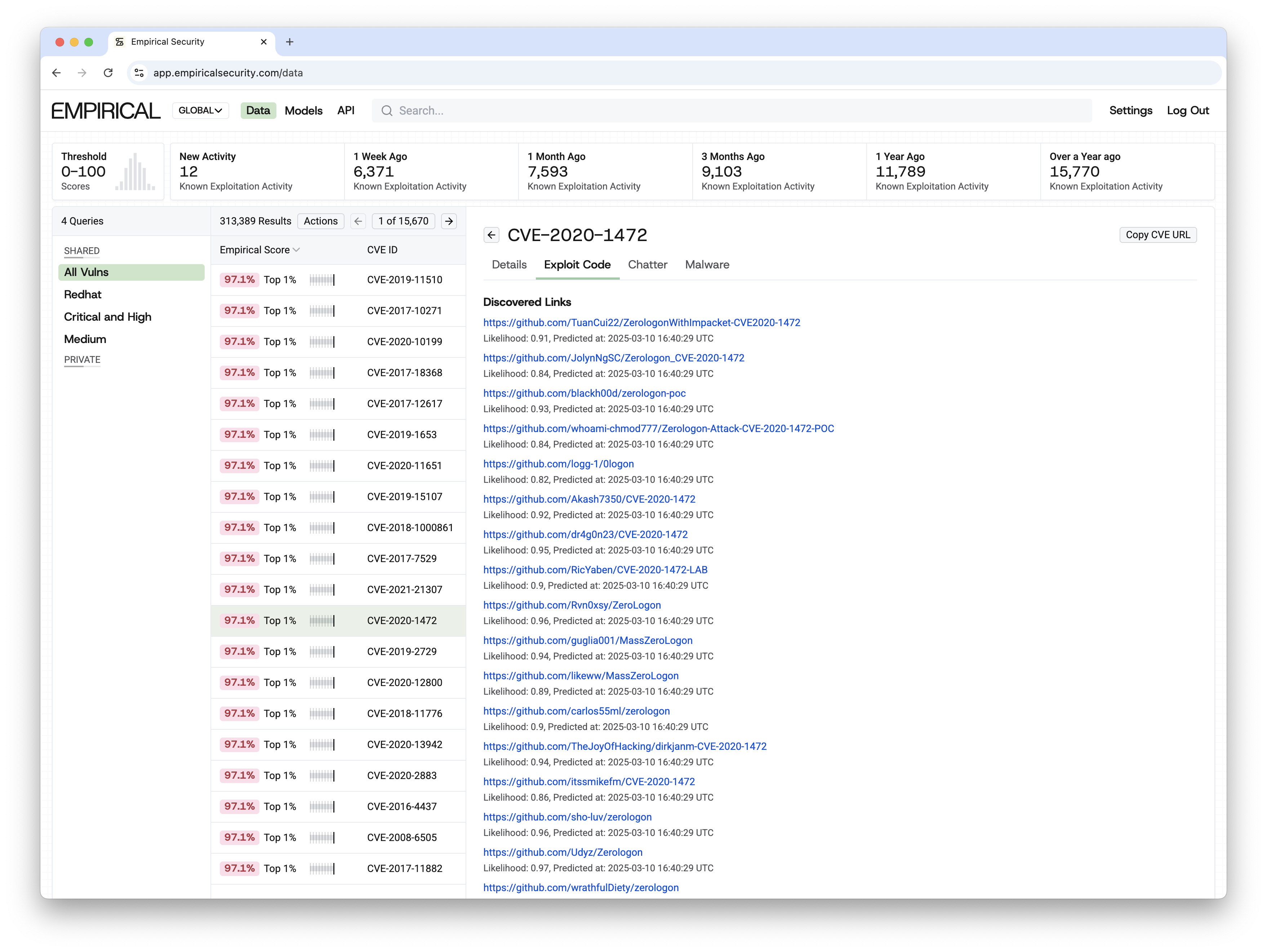
CVE Chatter Link Collection
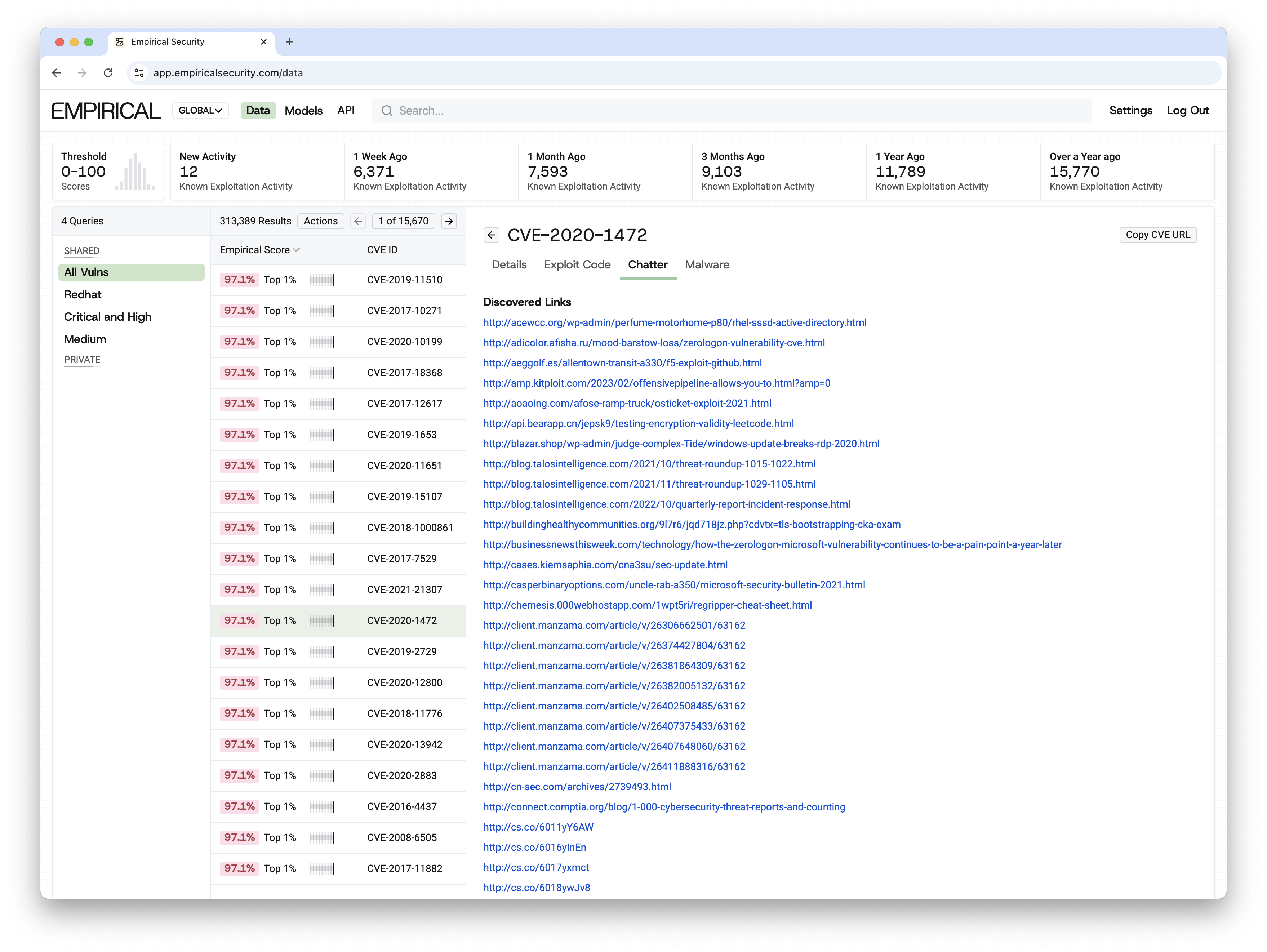
Malware Hash Database