
Avoid the exploitable CVEs. Beat the odds and win big.
Most teams lose this game, because vendor dashboards and CVSS scores keep teams flying blind.
Want to play the game better?
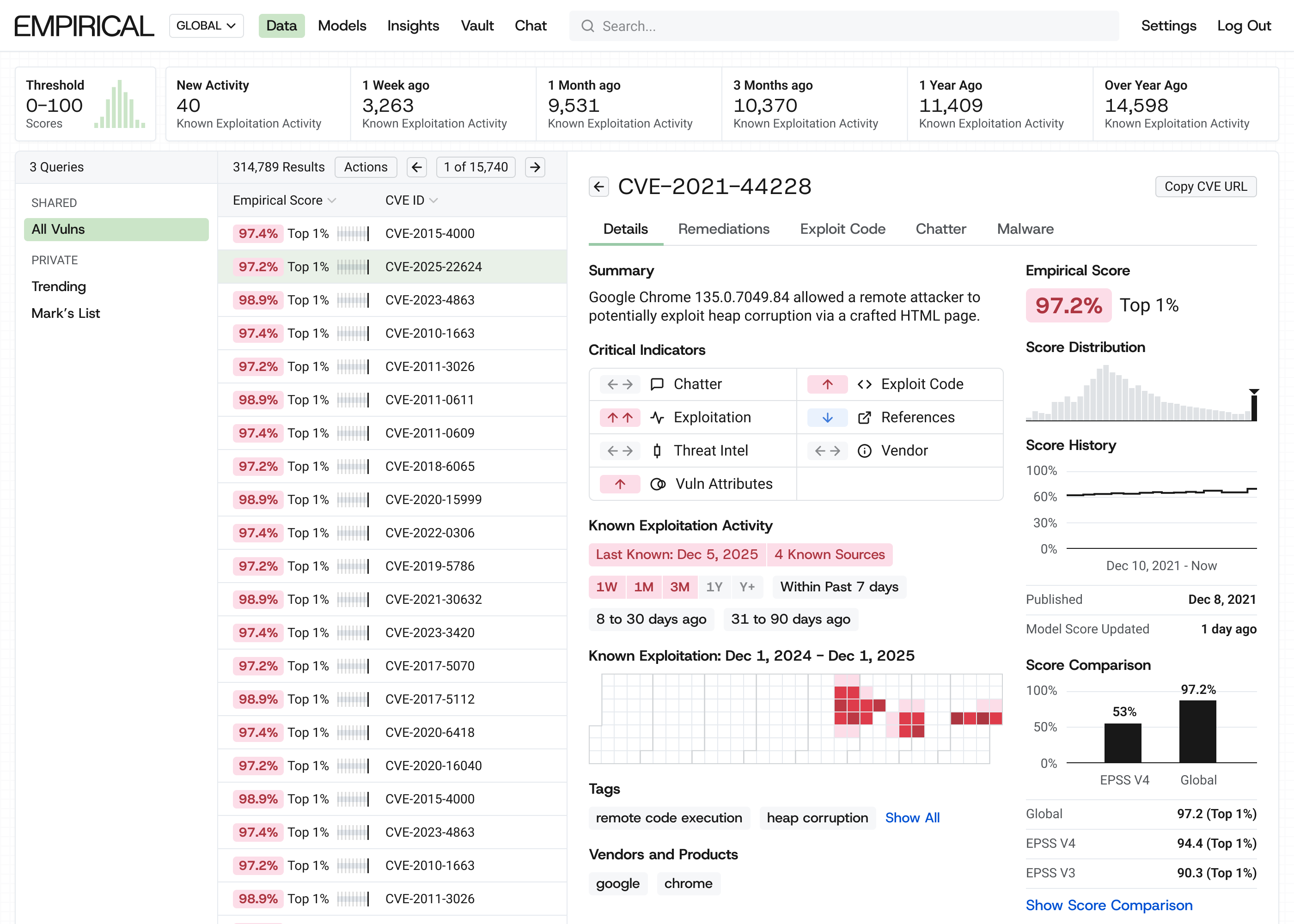
Identify and remediate the CVEs that are truly exploitable in your environment. Empirical uses data science and AI to model exploitability based on real-world conditions, not generic scores.
About Us
Empirical builds rigorous, data-driven models, specifically local models tailored to individual organizations. We leverage existing open-source technology (EPSS, used by over 120 vendors today) while offering proprietary global and local models.
Compare Model Features
ALL MODELS
EPSS
Global
Local
Predictive Vulnerability
Scoring
ALL MODELS
EPSS
Global
Local
Hourly Score Updates and Enterprise Support
ALL MODELS
EPSS
Global
Local
Legacy Model Support
(EPSS v3, v4)
ALL MODELS
EPSS
Global
Local
UI and API for Data Discovery & Model Performance
GLOBAL + LOCAL MODELS
EPSS
Global
Local
Data on over 17,000 exploited in the wild CVEs
GLOBAL + LOCAL MODELS
EPSS
Global
Local
Near-Real Time Exploitation Telemetry & Model
GLOBAL + LOCAL MODELS
EPSS
Global
Local
ML model for discovering new exploit code on GitHub
GLOBAL + LOCAL MODELS
EPSS
Global
Local
All Underlying data contributing to the model exposed
LOCAL MODELS
EPSS
Global
Local
Custom Vulnerability Model based on your attack telemetry, asset data, vuln data, & threat intelligence
LOCAL MODELS
EPSS
Global
Local
Model Performance Measured against your attack telemetry
LOCAL MODELS
EPSS
Global
Local
