Every Enterprise Is Unique. Your Risk Decisions
Should Reflect That.
Empirical builds data-driven models to prioritize, remediate, and summarize cybersecurity findings. We’re building the world’s first organization specific models for cybersecurity.
Our Models
CloseEPSS Model
EPSS provides a prediction of the probability of exploitation of a vulnerability. It uses data contributed by participating vendors and is the free and open model used by over 120 vendors to score vulnerabilities. Empirical maintains and trains the model.
Empirical Global Models
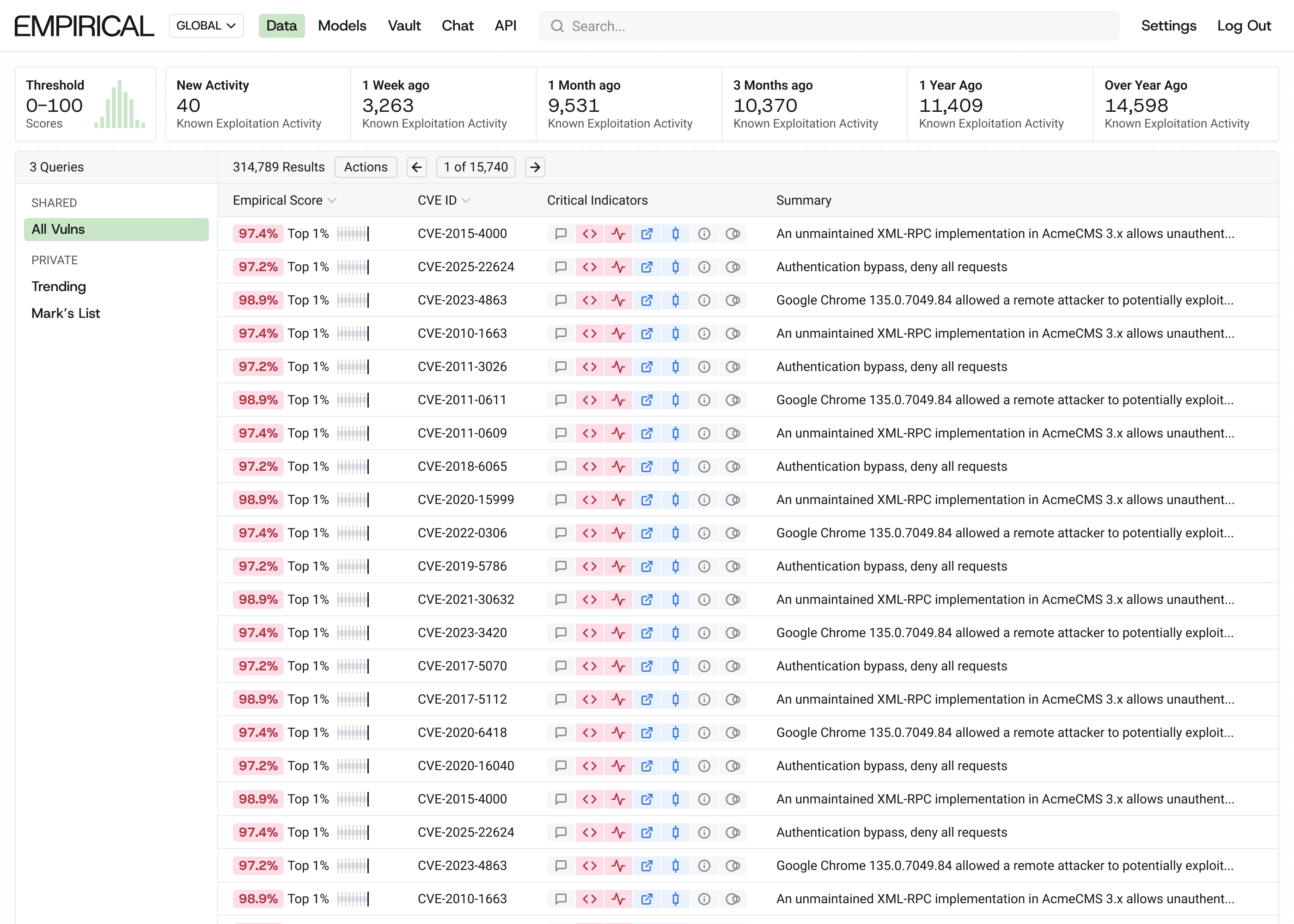
Global models combine real-time internet exploitation telemetry with EPSS predictions to provide the most accurate view of exploitation. It monitors activity over 17,000 known exploited in the wild CVEs, and uses that data in the model. This is 12x DHS CISA’s KEV, and far more than any other vendor out there.
Empirical Local Models
Your enterprise has environmental and telemetry data that should be used in decision making. Empirical unlocks the value of these datasets by training a local model, specific to you and only accessible by you, to support your enterprise’s decision making.
We bring measurable impact
Our models increase efficiency and coverage, reveal unknown threats, reduce risk, and optimize remediation capacity.
17,000+
Known Exploited Vulns (and hourly telemetry about when exploitation occurred)
12.4x
A 1249.04% increase in total exploited CVEs as of January 9th, 2025 compared to CISA Known Exploited Vulnerabilities (KEV)
23x
4925 newly exploited CVEs in the last 12 months, compared to 204 in CISA KEV
We're building the first domain and enterprise specific models in cybersecurity
Enterprises are unique. Security tools aren’t.
Every organization runs its own stack, faces different threats, and operates under different constraints. Yet most security products treat them the same—shipping generic rules and risk scores that ignore local context.
AI needs to be local, not just large.
Modern AI enables us to model security posture, asset value, and attacker behavior with real precision—but only if we adapt to the enterprise’s actual environment. Local models let us reflect your infrastructure, your priorities, and your risk—not someone else’s.
Static logic can’t keep up.
Traditional security tools rely on static playbooks and CVSS scores, producing the same alerts everywhere. That’s why teams drown in backlogs while attackers move faster. Local, adaptive models cut through the noise and surface what really matters—for your environment.
Our Products
01
EPSS Model
Empirical builds and maintains the world’s only public machine learning model in cybersecurity, EPSS.
02
Global Models
Global models combine real-time exploitation telemetry with EPSS predictions to accurately depict exploitation.
03
Local Models
Local models are trained on your environmental and telemetry data to support your enterprise’s decision making.